Bad news for WordPress users – Recently, on December 11, 2019, researchers discovered an authentication vulnerability on 2 plugins, Elementor and Beaver Builder. Does this vulnerability affect your website and how can you fix it? Let’s find out more about this issue with AZDIGI!
Authentication vulnerability in Elementor and Beaver Builder
Security researchers have discovered a critical authentication vulnerability that is easily exploited in 2 plugins, “Ultimate Addons for Beaver Builder” and “Ultimate Addons for Elementor”. What is more concerning is that attackers have already started exploiting this vulnerability within 2 days of its discovery to compromise vulnerable websites and have quickly installed a malicious backdoor for immediate access.
Both plugins are developed by software development company Brainstorm Force and currently power hundreds of thousands of WordPress websites using the Elementor and Beaver Builder frameworks – helping administrators and designers expand the functionality of websites with various widgets, modules, and templates.
According to researchers, the vulnerability in both plugins allows WordPress account owners including administrators to authenticate via Facebook and Google login mechanisms.
However, due to the lack of authentication checks when logging in via Facebook and Google, the plugins are more vulnerable to attacks. It allows all users to log in without any passwords, even if they are malicious.
In addition, Facebook and Google’s authentication methods have been verified through verification codes instead of passwords, so passwords are not checked during authentication.
How do hackers exploit vulnerabilities in Elementor and Beaver Builder?
To exploit this vulnerability, hackers need to use the email ID of the website administrator. And in most cases, this information can be easily accessed.
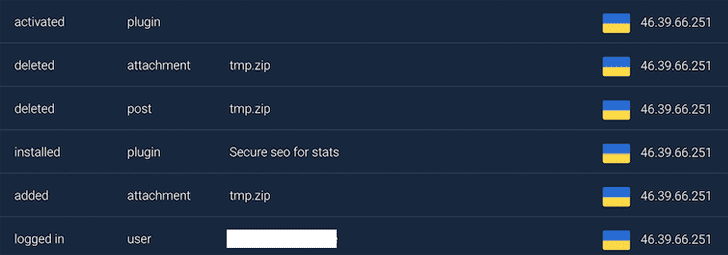
Thanks to this, they have exploited this vulnerability to infiltrate websites, install fake SEO tracking plugins after uploading the tmp.zip file on the WordPress server that was previously targeted. Finally, they will release the blacklink wp-xmlrpc.php file into the root directory.
Fortunately, MalCare discovered the vulnerability on December 11, 2019 and quickly addressed the issue by releasing patches for both plugins within just 7 hours.
The authentication bypass vulnerability was patched by releasing “Ultimate Addons for Elementor version 1.20.1” and “Ultimate Addons for Beaver Builder version 1.24.1“.
To prevent hackers from exploiting the authentication bypass vulnerability, WordPress websites using these 2 plugins should update to the latest versions to patch the vulnerability and avoid potential damage to their websites.
Please regularly follow AZDIGI‘s fanpage and blog to stay updated on the latest news and promotions! Thanks for reading the article!

