Nội dung
Configuring Google Authenticator SSH on CentOS 7, aka 2-factor authentication, brings more safety and security to VPS administration and your data. In this article, AZDIGI will show you how to enable 2-factor authentication when SSH-ing into your system.
I. Overview
What is 2-factor authentication?
Two-Factor Security, or 2FA for short, is an extra step in your regular login activity. Without 2FA, you will only enter your username and password to log into the system, your account. The password section will be the only layer of protection for the account. Meanwhile, the added second layer of security will help you better protect your account.
Why should you use 2-factor security?
Two-factor security is the best way to protect yourself from attacks that steal sensitive user account information, spoof login pages, and other account-hijacking methods. With 2-factor security, you can be more assured if your account information is accidentally exposed In addition, it will be difficult for others to access your accounts because there will be obstacles in the 2-factor security step.
In this article, AZDIGI will show you how to set up 2-factor authentication when SSH-ing into your VPS server, this helps increase the security of your VPS if your root information is accidentally exposed. For details, please refer to part II.
II. Implementation Guide
To set up Google Authenticator, you can follow these 4 steps.
Step 1: SSH into your server
First, you need to SSH into your VPS as root, if you don’t know how to SSH, you can see the instructions below:
After SSH is successful, you continue to Step 2.
Step 2: Set up Google Authenticator
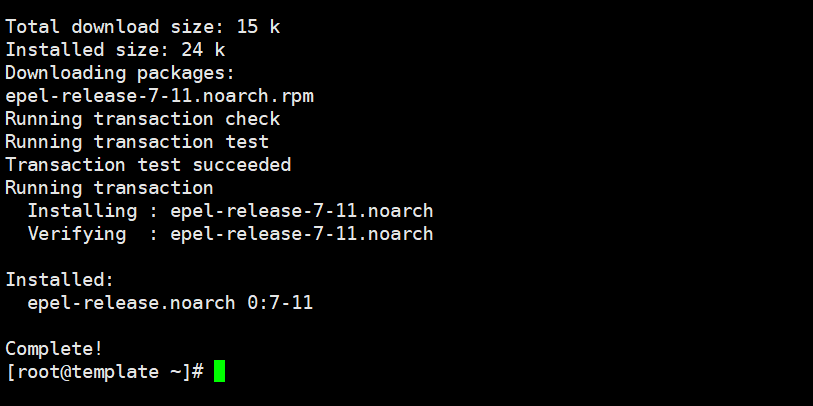
- Install the epel-release repo
yum install -y epel-release
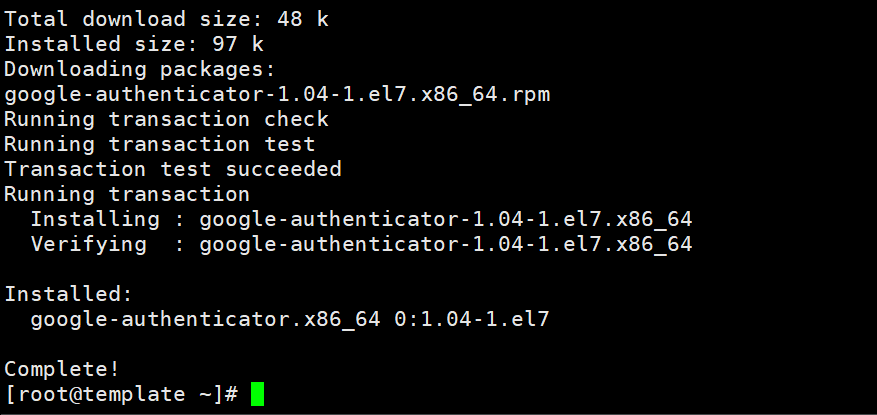
- Install pack google-authenticator
yum install -y google-authenticator
- Run the following command after the installation is complete to generate the secret key.
google-authenticator
- Next, the system will ask you to confirm and provide a QR code.
[root@template ~]# google-authenticator Do you want authentication tokens to be time-based (y/n) y Warning: pasting the following URL into your browser exposes the OTP secret to Google: https://www.google.com/chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/root@template.azdigilab.com%3Fsecret%3D57C7LI5GMEY4UXG4AZIKKKUXDQ%26issuer%3Dtemplate.azdigilab.com Your new secret key is: 57C7LI5GMEY4UXG4AZIKKKUXDQ Your verification code is 729816 Your emergency scratch codes are: 13966703 30305338 70660643 75967179 72069190 Do you want me to update your "/root/.google_authenticator" file? (y/n) y Do you want to disallow multiple uses of the same authentication token? This restricts you to one login about every 30s, but it increases your chances to notice or even prevent man-in-the-middle attacks (y/n) y By default, a new token is generated every 30 seconds by the mobile app. In order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. This allows for a time skew of up to 30 seconds between authentication server and client. If you experience problems with poor time synchronization, you can increase the window from its default size of 3 permitted codes (one previous code, the current code, the next code) to 17 permitted codes (the 8 previous codes, the current code, and the 8 next codes). This will permit for a time skew of up to 4 minutes between client and server. Do you want to do so? (y/n) y If the computer that you are logging into isn't hardened against brute-force login attempts, you can enable rate-limiting for the authentication module. By default, this limits attackers to no more than 3 login attempts every 30s. Do you want to enable rate-limiting? (y/n) y

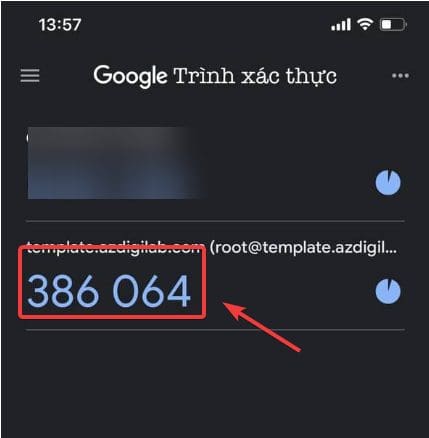
- You open the Authenticator app and scan the QR code displayed on your VPS.
When you scan the above QR code, we will receive a 6-digit code, these 6 digits will continuously change after 30 seconds.
Step 3: Set up VPS to allow authentication through Google Authenticator
To set up VPS to allow Google Authenticator authentication when SSH, you move and edit the file /etc/pam.d/sshd
vi /etc/pam.d/sshd
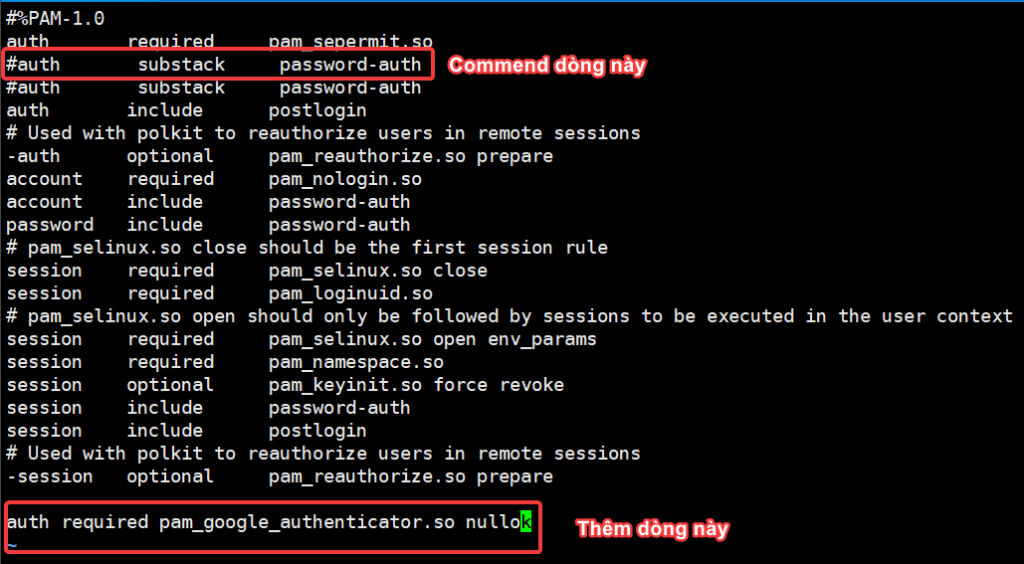
- Add and comment on the following lines in the/etc/pam.d/sshd file
Add line: auth required pam_google_authenticator.so nullok
Commend line: auth substack password-auth.
- Proceed to edit the /etc/ssh/sshd_config file
- Find the line ChallengeResponseAuthentication, change the setting from no to yes
- Add the new line AuthenticationMethods publickey,keyboard-interactive.
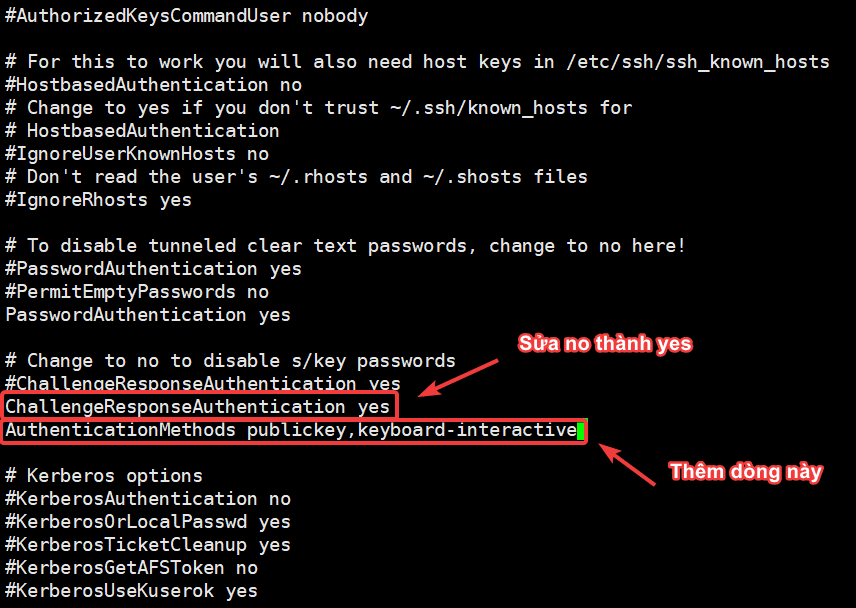
- Restart the sshd service after editing.
systemctl restart sshd
Step 4: Check the Authenticator operation when SSH
After completing the configuration, you need to exit the VPS and log in again to check. When logging in, the OTP code will be generated on the Google Authenticator app, you just need to enter this code to be able to SSH.
III. Summary
So in this article, AZDIGI showed you how to install 2-factor authentication when SSH-ing into VPS, this helps to increase security and reduce the risk of password detection attacks. With 2-factor authentication, you can rest assured that even if your root information is accidentally exposed, others will not be able to SSH into your VPS without the 2-factor authentication code. If you find this article interesting and useful, you can share it widely.
To see some other useful articles on Linux VPS administration, you can visit the link below:
If you need assistance, you can contact support in the ways below:
- Hotline 247: 028 888 24768 (Ext 0)
- Ticket/Email: You use the email to register for the service and send it directly to: support@azdigi.com .

