Nội dung

From DirectAdmin version 1.61.0 onwards, there is support for jailed shell and jailed cron to limit user rights on DirectAdmin. To use jailed shell and jailed cron requires BubbleWrap, it will help create an extra layer of protection and restrict user rights on the Linux server.
Introduction
BubbleWrap is running an application like in a sandbox, docker, etc. that has been set up to restrict access to the system or user data.
BubbleWrap works by creating a completely new space located in the clipboard and invisible from the host and will be automatically deleted when the last process exits.
Using BubbleWrap, you can specify which filesystem parts should be displayed in the sandbox.
BubbleWrap doesn’t allow upgrading privileges.
Applications work without permission (escalation), even when used with proprietary software installed on the accompanying OS.
Steps to setup DirectAdmin user rights restrictions
In this tutorial, I set up DirectAdmin user rights restrictions on CentOS 7.
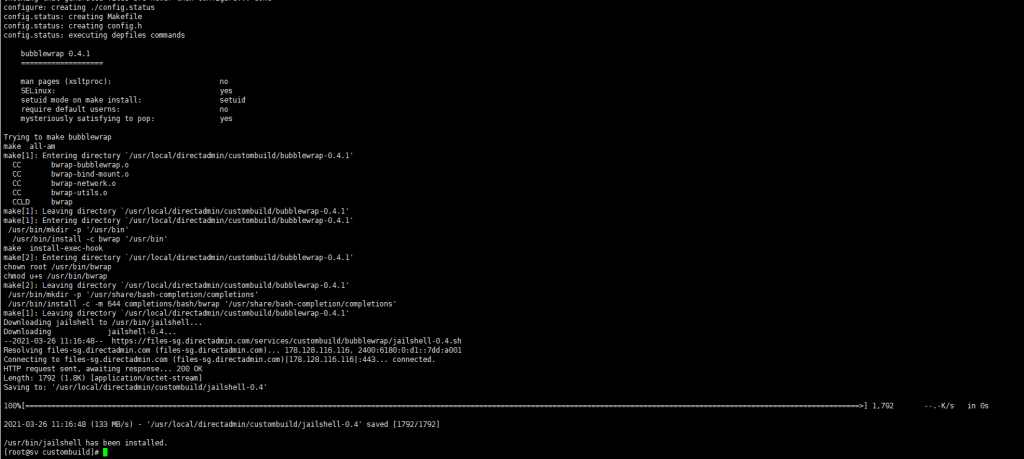
Step 1: Build bubblewrap
Go to DirectAdmin and move into custombuild directory. Copy the commands below with root user privileges.
cd /usr/local/directadmin/custombuild
./build update
./build bubblewrap
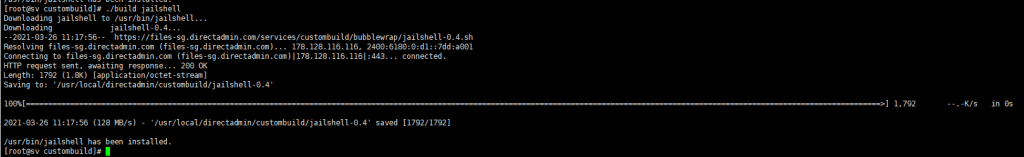
Step 2: Build jailshell
Please copy the commands below to execute the build jailshell.
cd /usr/local/directadmin/custombuild
./build jailshell
Step 3: Enable the user permission limitation function in DirectAdmin
DirectAdmin will create the default value “jail” (set to 0 by default). Set the value to 1 to enable the function of limiting user permission for DirectAdmin.
/usr/local/directadmin/directadmin set jail 1 restart
service directadmin restart
Or you can directly access the user.conf file of each user to edit user.conf jail=ON/OFF /users/namnhh/user.conf
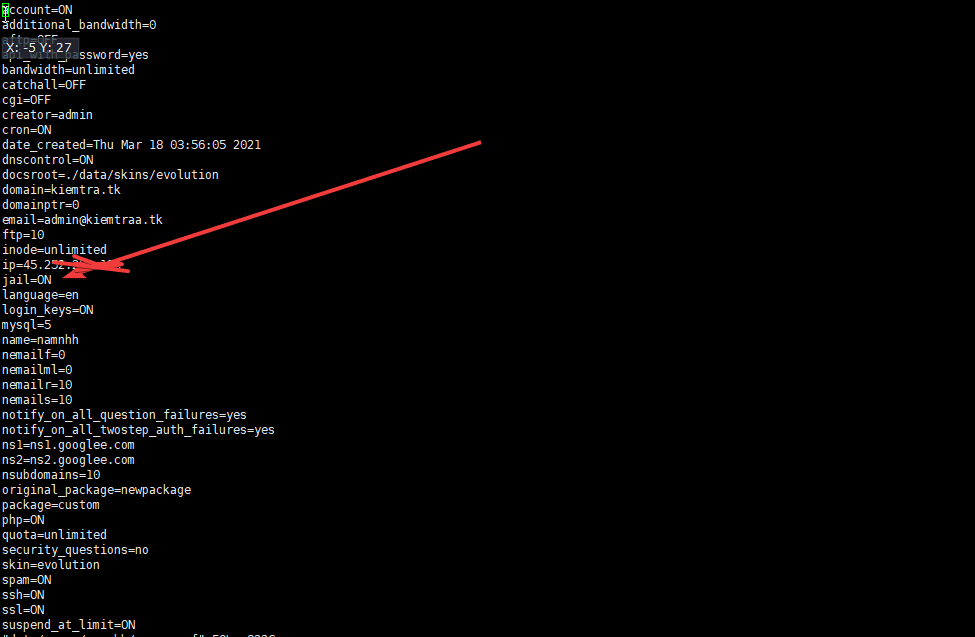
To enable or disable restricting DirectAdmin user permission, go to the modify account section:
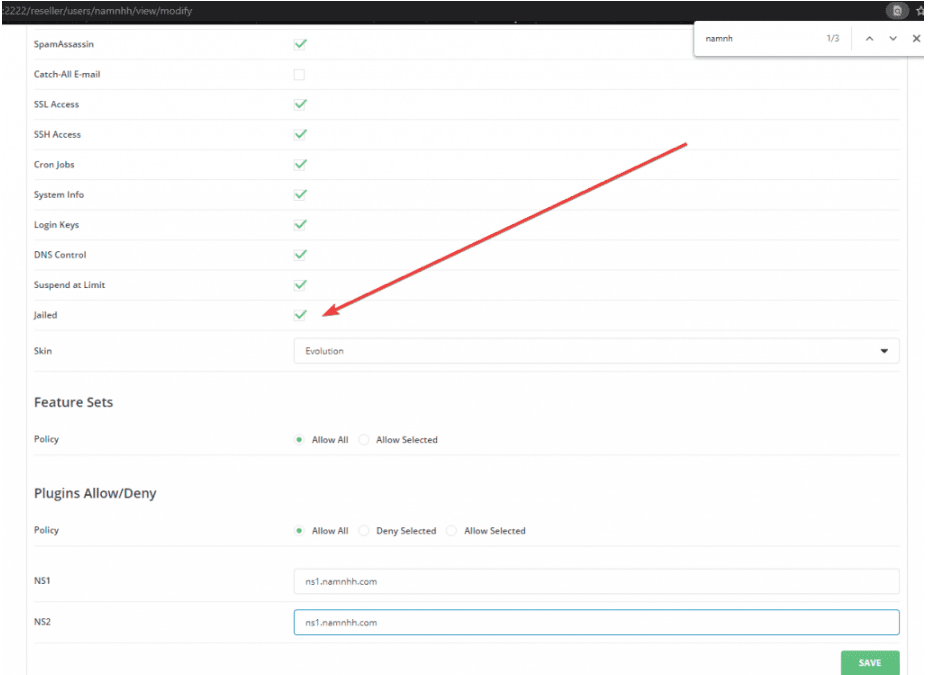
/usr/local/directadmin/directadmin set jail 1 restart
## Lưu ý khi set giá trị bằng 1 thì các user không áp dụng hết cần phải tick chọn hoặc làm bằng thủ công như hướng dẫn
To enable all users (Force) to limit DirectAdmin user permissions, set jail to 2.
/usr/local/directadmin/directadmin set jail 2 restart
service directadmin restart
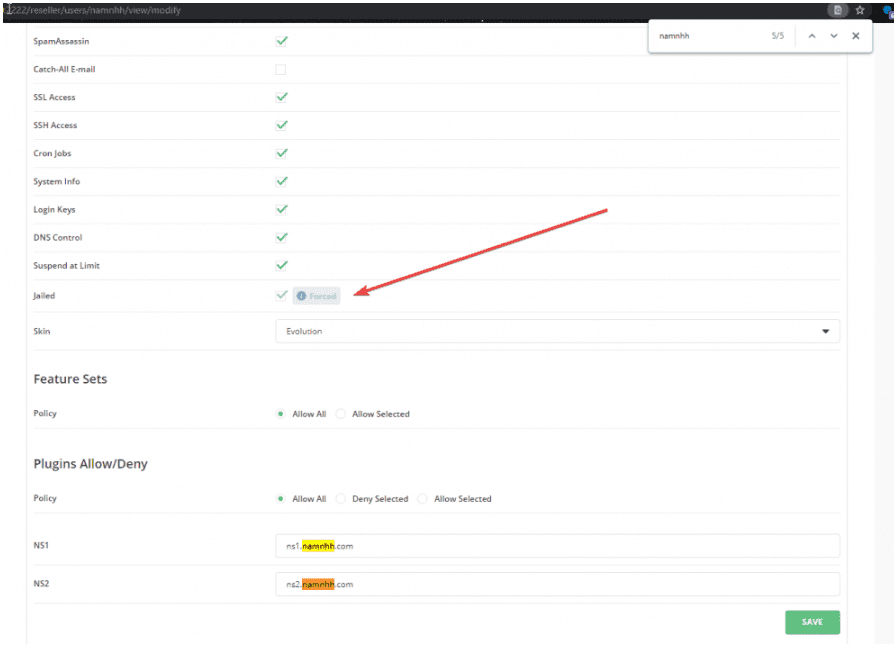
When you go to the modify account section, you will see the difference between the two values when setting 1 and 2.
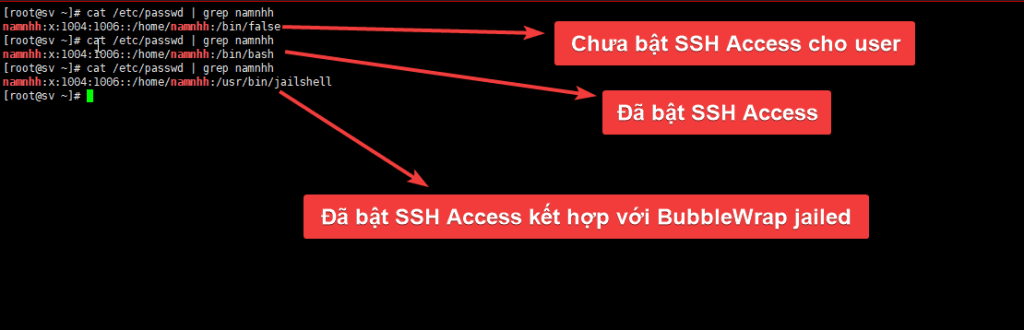
Step 4: Recheck the user when ssh access and jail are enabled
To check, please access the file /etc/passwd, you will see that it has enabled the DirectAdmin user permission limitation.
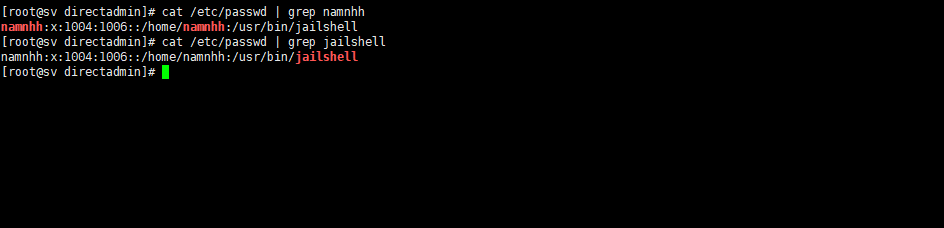
cat /etc/passwd | grep namnhh
cat /etc/passwd | grep jailshell
Hoặc dùng câu lệnh bên dưới
grep -e "namnhh" -e "jailshell" /etc/passwd
After checking your user as shown above, you have successfully configured the user permission limitation for DirectAdmin.
Summary
Limiting user permissions DirectAdmin is a security measure to restrict users when allowing users to use SSH in the server.
Jailed users cannot access the home directory of other users.
Jailed users can still run all the necessary commands from the main shell on their users.
Hopefully, this article helps you to secure your server better when shell attacks infect other users.
See more useful articles about DirectAdmin at the following link:
If you need assistance, you can contact support in the ways below:
- Hotline 247: 028 888 24768 (Ext 0)
- Ticket/Email: You use the email to register for the service and send it directly to: support@azdigi.com .
- Website AZDIGI: https://azdigi.com/

