While using Hosting services, providers often turn on security features to help customers’ websites be more secure and minimize the risk of attacks.
One of the most common security features on hosting is the ModSecurity tool, which acts as a website firewall (WAF). In this article, let’s learn about ModSecurity with AZDIGI and how to enable/disable ModSecurity on Hosting.
What is ModSecurity?
ModSecurity is a web application firewall (WAF). When a request is sent, ModSecurity will analyze that request based on the Request header, Request body components to see if these requests are valid or not. Any requested information in each section violates the set rules, it will be up to the configurator to respond accordingly. That is, if your website receives a request that is suspiciously malicious or is trying to attack, ModSecurity will block that request if it has predefined rules.
Most hosting services at AZDIGI are equipped with this feature to block basic attacks such as Brute-force, XSS, SQL Injection,…
Normally, ModSecurity will be enabled on your Hosting, but in some cases, you manipulate your website (manipulate too fast or for other reasons), causing Hosting to mistake you as the person trying to invade Hosting. This feature will do your own blocking; the usual error you get is 403 error in this case.
How to enable/disable ModSecurity
To enable/disable it, go to cPanel => find the ModSecurity item.
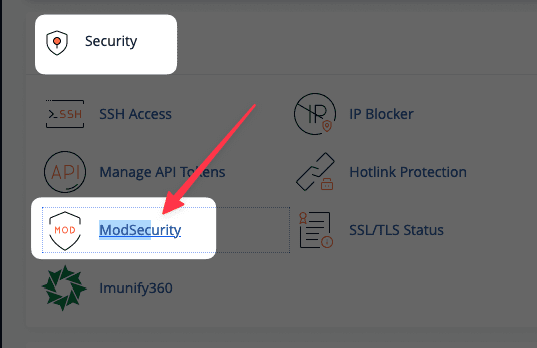
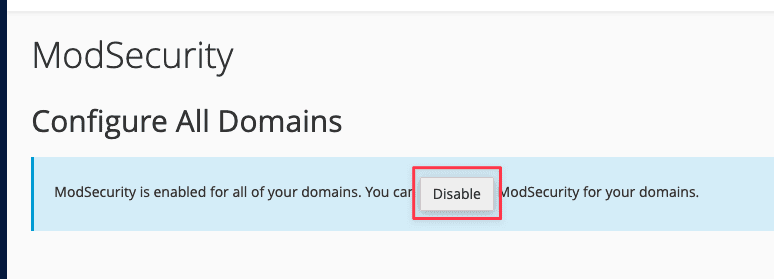
Next, click Disable or Enable, depending on your needs.
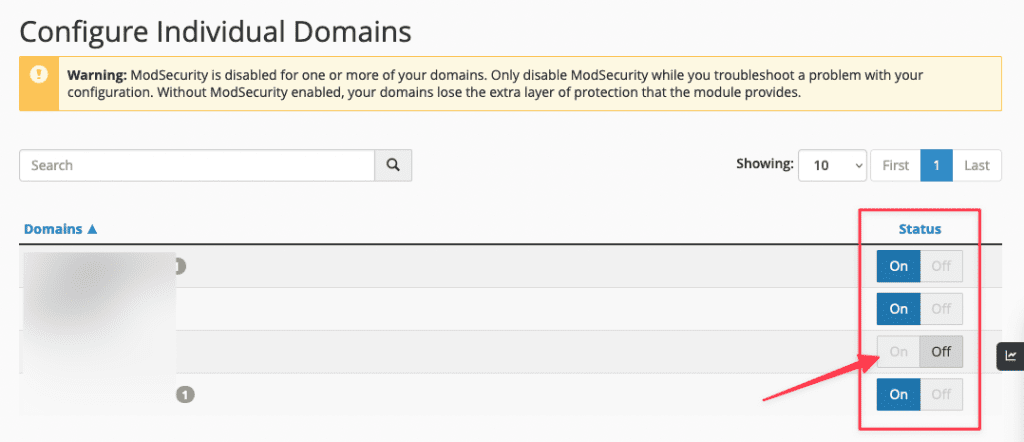
If you just want to enable/disable ModSecurity for each individual website, you can select the On/Off button at the bottom.
ModSecurity is an open-source web-based firewall (or WAF) application supported by various web servers: Apache, Nginx and IIS. You should enable this function during your Hosting usage to get the most out of the ways to prevent attacks on your web hosting.

