Nội dung
For attackers, the website can be seen as a valuable data store, they can make a lot or even a lot of money from the data on your website. However, the website will not be vulnerable to exploitation if it is tightly protected and does not have any vulnerabilities for attackers.
WAF (Web Application Firewall) Website protection application is one such tool, it helps you limit and control hackers and create a secure connection before everything goes to your website and you can be found WAF at AZIGI hosting services. So let’s explore WAF with us now!
What is WAF?
WAF (Web Application Firewall) or more familiarly known as website firewall – is considered one of the important factors to help you avoid the fear of targeted website attacks.
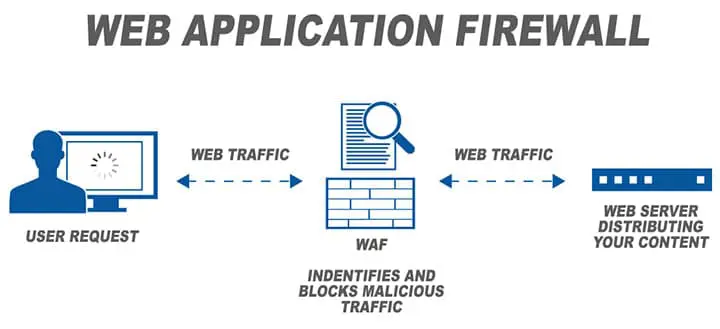
In simpler words, WAF is likened to a barrier between the user and the website, it helps you prevent and remove malicious requests before reaching your website. All requests from outside are strictly controlled and checked by them to minimize the risk of data coming from attackers.
However, you need to distinguish between a Network Firewall and a WAF that is different! Although in fact, there are many good types of network firewalls today, they have the disadvantage that they do not understand HTTP and so they cannot detect specific attacks that target security flaws in web applications.
With WAF, however, it can help you strengthen your web security in a way that network firewalls cannot.
7 network layers according to the OSI model
As you can imagine, the Internet has many different layers, and to protect them, you need to combine different suitable security tools to protect the individual layers.
Below we will analyze according to the OSI model so that you can better understand the network security layers as well as the role of WAF in website security.
What is the OSI model? The OSI model is a framework that divides the overall knowledge of the network into seven different parts.
7 network layers are divided according to the OSI model
| 7. Application Layer | User-computer interaction layer: Applications can access network services |
| 6. Presentation Layer | Make sure the data is in a usable format and where data encryption occurs. |
| 5. Session Layer | Maintain connections: responsible for controlling ports and sessions |
| 4. Transport Layer | Transferring data using transmission protocols |
| 3. Network Layer | Decide which physical path the data will take. |
| 2. Datalink Layer | Specifies the format of the data on the network. |
| 1. Physical Layer | Transmit raw bit stream over physical medium |
Although these 7 layers have different roles, they all play a very important role in protecting your website. With normal Network Firewall will help you with layer 3 and 4 protection, while WFA supports layer 7 protection.
WAF can also work network-based (hardware), software-based or Cloud-based, which can be seen, the nature of WAF is virtual or physical.
Why can WAF do that?
1. Security model
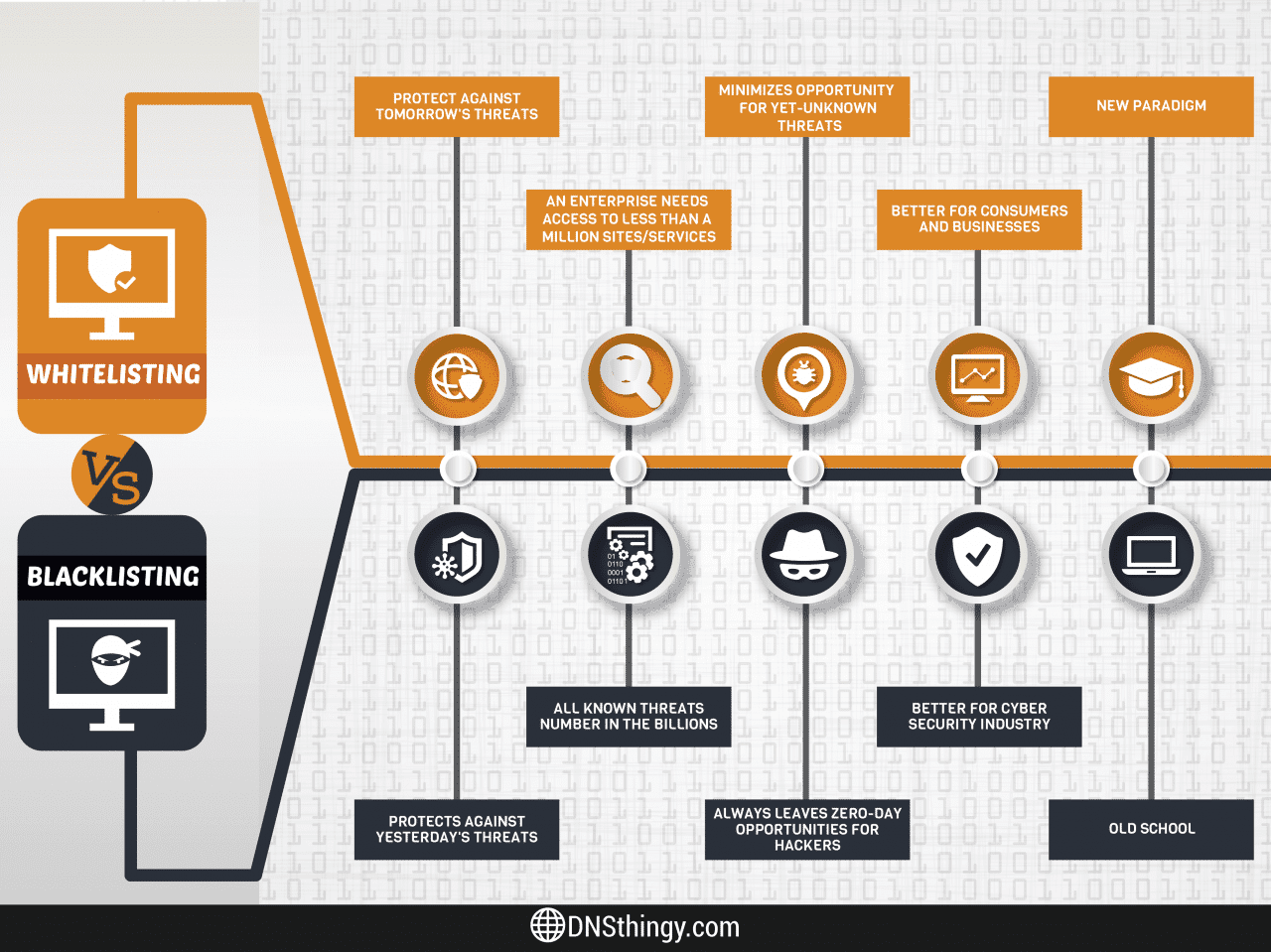
There are many WAF security models that can filter and block malicious data and prevent them from entering your websites, such as the Blacklist model or the Whitelist model.
Blacklist: A collection of lists of unwanted IP addresses or user agents that your WAF automatically blocks.
Whitelist: In contrast to Blacklist, Whitelist allows users to create an exclusive list of IPs and user agents that are allowed to access. The rest will be rejected.
Because both security models above have their own advantages and disadvantages, WAF has provided a model that combines Blacklist and Whitelist.
2. Be equipped with a strict policy and set of rules
WAF Equipped with a set of rules to determine who your friends are and who is causing trouble for your site. From there, they help you eliminate troublemakers to keep your website safe.
These policies will combine rule-based logic, parsing, and signatures to help detect and prevent a number of different web application attacks.
WAF in particular is well known for protecting against some of today’s top web application security risks. It includes malicious attacks such as cross-site request forgery, cross-site-scripting XSS, file and SQL injections.
The WAF’s Virtual Patch is also an effective defense, it’s essentially a set of rules that help address vulnerabilities in software without having to manually tweak the code.
Meet legal security criteria for businesses
In addition to providing rules and security models to prevent intruders, WAF has also become one of the standards to help meet legal security criteria such as credit card information, personal information. , business information….helps businesses complete the regulatory standards of PCI, HIPAA and GDPR.
Does AZDIGI HOSTING have a WAF?
If you don’t know yet Imunify360 is a set of WAF has been integrated by AZDIGI for a long time in all hosting packages that integrate WAF rules to combat the risks of exploiting common vulnerabilities of hackers or malicious data.

