Nội dung
Part 1: Introduction
What is DDoS?
DDoS stand for Distributed Denial of Service, which means distributed denial of service. This is a concept to refer to a new type of server attack that has appeared recently. Hackers through one computer to penetrate, control millions of other computers to access a server, increase traffic, lead to exhaustion of bandwidth and server resources.
DDoS attackers not only use their own computers to carry out attacks but also make the victim’s computer perform this attack behavior. These hackers will take control of the victim’s computer to send a large amount of data or requests to a specific website or email address.
Some common types of DDoS attacks
Currently, hackers often use popular types of DDoS attacks as follows:
- SYN Flood: A type of attack with the aim of exploiting the weakness of the TCP connection protocol. When hackers attack this way, fake messages will be sent to the server continuously, causing the connection to be unable to close, leading to the service being crashed.
- HTTP Flood: A type of DDoS attack by sending many Post or Get requests to the server, forcing the server to use maximum resources for processing.
- UDP Flood: The result of this type of attack is UDP flooding. Hackers using this type of attack will send large amounts of UDP to random ports of the server, overloading the server and eventually denying service.
- Fraggle Attack: An attack by sending a large amount of UDP to the server, overloading, leading to system congestion.
- Application Level Attack: A type of attack on the security holes of the operating system and network devices.
- Advanced Persistent Dos (APDos): An attack that combines many forms of attack such as SYN Flood, HTTP Flood,…
- Ping of Death: With this type of attack, the hacker will overload the server by sending ICMP of more than 65,536 bytes to the server. This packet size is quite large, so it will be broken down to send. When it reaches the server, the splits will be merged, resulting in a cache overload that causes the server to crash. This type of attack is often combined with the Smurf Attack.
- Slowloris: A form of attack that sends many incomplete HTTP requests and maintains the connection for a long time, so the server is overloaded, refusing other service connection requests.
- NTP Amplification: An attack with a feature vulnerability of the computer system connected to NTP, causing the website’s server to be overloaded.
- Zero-day DDos Attack: A form of overloading the server by attacking the server’s security holes.
How to recognize a DDoS attack
One of the following signs that your website/server may be under a DDoS attack:
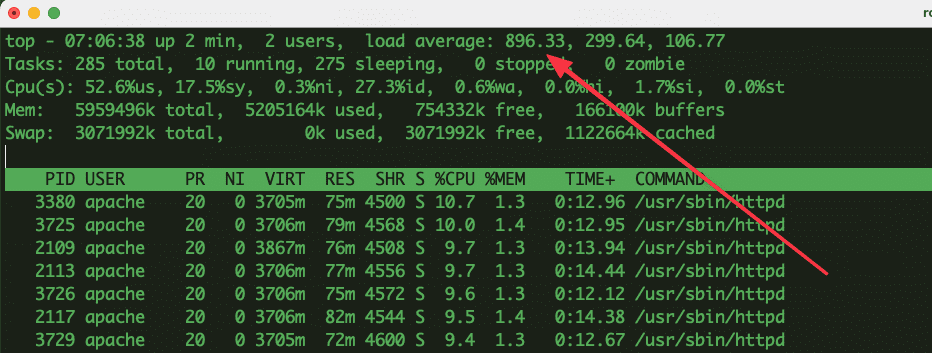
- The server has a lag situation and the CPU (Load average) load is unusually high.
- One or more websites are slow or inaccessible.
- Internet connection is slower than usual, taking a long time to access.
Below is an example of a website under a DDoS attack whose load average is unusually high.
Part 2: Using CloudFlare to prevent DDoS attacks
Check the log and determine the form of attack
To determine if your website/server is under DDoS attack, you need to check the log from the server to determine and take an appropriate solution.
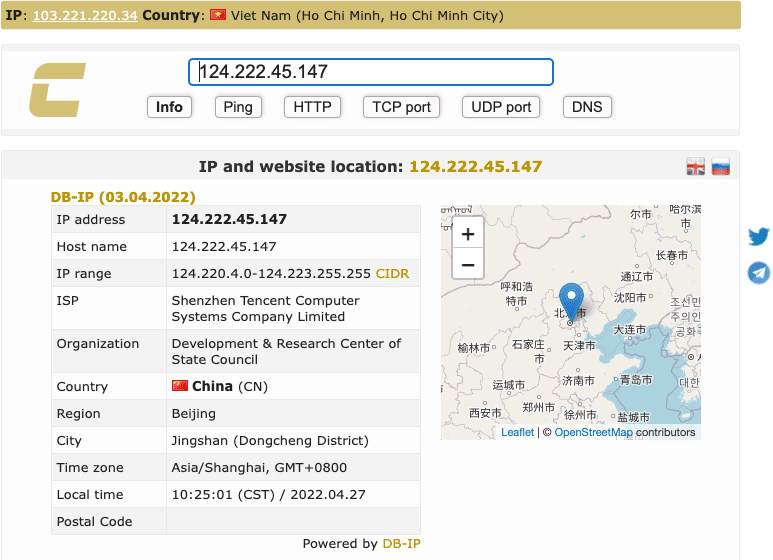
Below is the log that I can check from the Server, you can see that the log shows a lot of hits from many different IP sources, most of these IPs are from China. And this form of DDoS attack uses HTTP Flood (sends a large number of Post or Get requests to the server)
222.187.74.212 -[25/Apr/2022:21:12:01 +0700] "POST /?150288623887fmvujymq58607009924n64610761613foqdjaalp246389713767p117159001979lawxwzohz3060087145q72394190817=g116652528537j248517363287 HTTP/1.0" 302 581 "https://xxxx.net/" "Mozzila 5.0 (Linux; Android 5.0; SAMSUNG SM-G900F Build/LRX21T) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.4932.47 Safari/537.36"
124.222.45.147 -[25/Apr/2022:21:12:01 +0700] "GET /?264071997727ytuhwnkh22809370002l83389854653bxrapkork73899884685d18742915638bvsiiwqxi75944175718e148229866830=d142112181082a138522131506 HTTP/1.0" 302 581 "https://xxxx.net/" "Mozzila 5.0 (iPod touch; iPhone OS 4.3.3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4031.40 Safari/537.36"
180.124.152.107 -[25/Apr/2022:21:12:01 +0700] "HEAD /?186438297571umipitqt24133747303h245347765834ctwzlvtpf144399798184l225557017409uxxudfped82053913654j260424377140=x189688015618c37894054043 HTTP/1.0" 302 562 "https://xxxx.net/" "Mozzila 5.0 (Linux; Android 4.2.1; Nexus 5 Build/JOP40D) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.4857.50 Safari/537.36"
180.124.158.55 -[25/Apr/2022:21:12:01 +0700] "GET /?234465640857rmxjuoih263781470752z199637401324zbxscgqxd79173585438k96488125395sonubpsrb123130311913c260877257556=t94836647206j106990307316 HTTP/1.0" 302 581 "https://xxxx.net/" "Mozzila 5.0 (Windows NT 6.3; WOW64; rv:13.37) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/75.0.4153.58 Safari/537.36"You can check the source of the IPs at the link: https://check-host.net/
After determining the cause and type of attack, you can now continue to Step 2 to process this issue.
Use CloudFlare to block DDoS
Surely you will wonder, why not use the Firewall feature available on the server to prevent DDoS, but use CloudFlare. As you can see, the log records that the website is hacked from many different IPs and the origin of these IPs are all from China, but your users or customers are not from this market, so using Firewall to block each IP is unfeasible and ineffective. Therefore, it’s better that you need to block access by country, but currently this feature on Firewalls on the server is not as effective as CloudFlare.
I will show you to use CloudFlare’s Firewall to support DDoS prevention. Although it is only a free version, you will surely be surprised by Cloudflare’s results. If you don’t know how to use CloudFlare, you can refer to the articles about CloudFlare below:
Here are some ways to block DDoS that you can refer to:
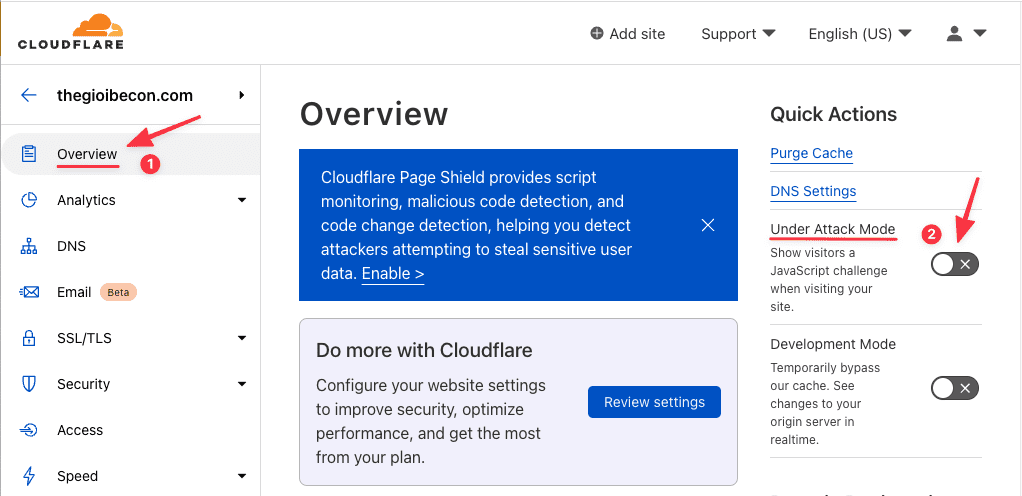
Turn on Under Attack Mode
On CloudFlare there is an anti-DDoS feature called Under Attack Mode, when using this feature, the browser will display a check step for 2-3 seconds and then allow you to access the website.
You can refer to the instructions to enable this feature as shown below:
Block access by specific Country
It would help if you used this solution when multiple IPs attack your website and those IPs originate from one or several specific countries. However, due to a large number of IPs and constantly changing, we will not be able to block each IP, but instead you should block access to that country as it is more feasible.
To configure, you need to access Security >> Firewall Rules >> Create firewall rule.
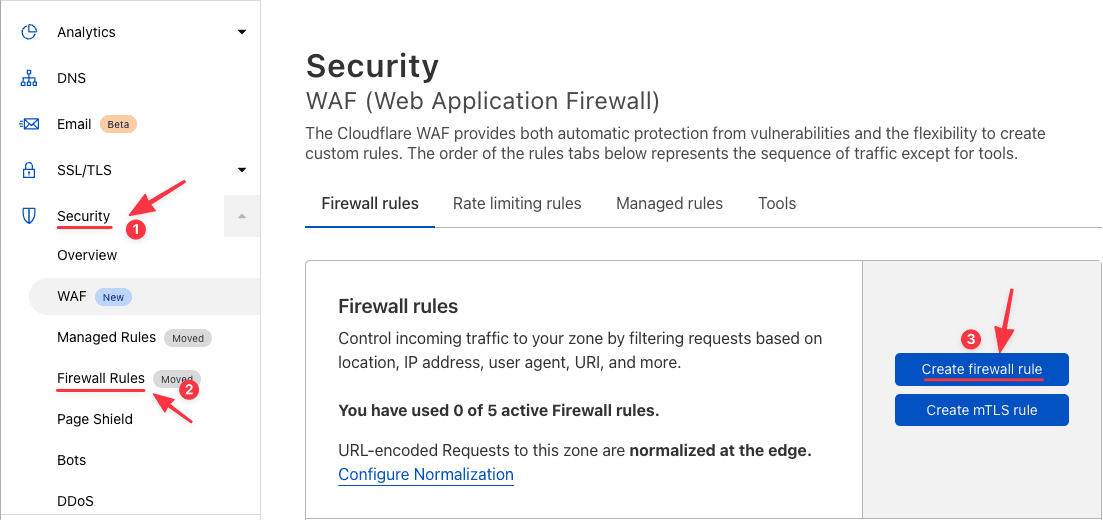
In the Create firewall rule creation section, you set the following:
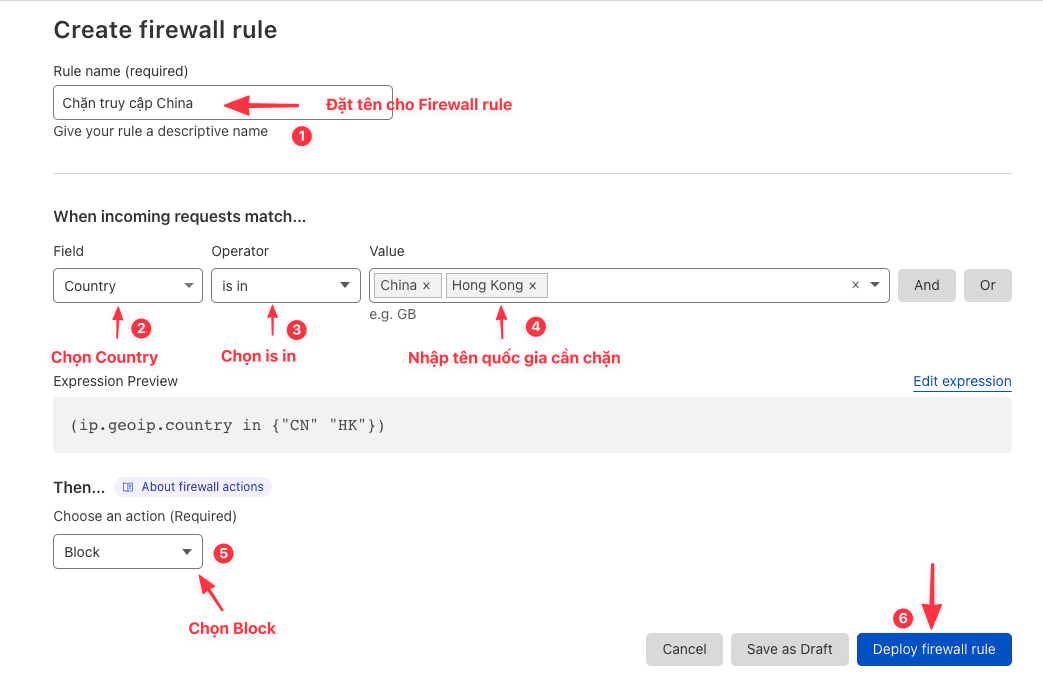
Once set up, the result will be as shown below:
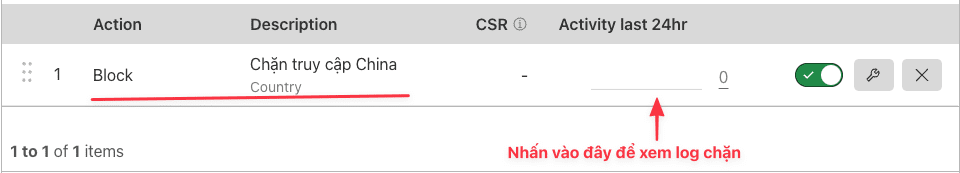
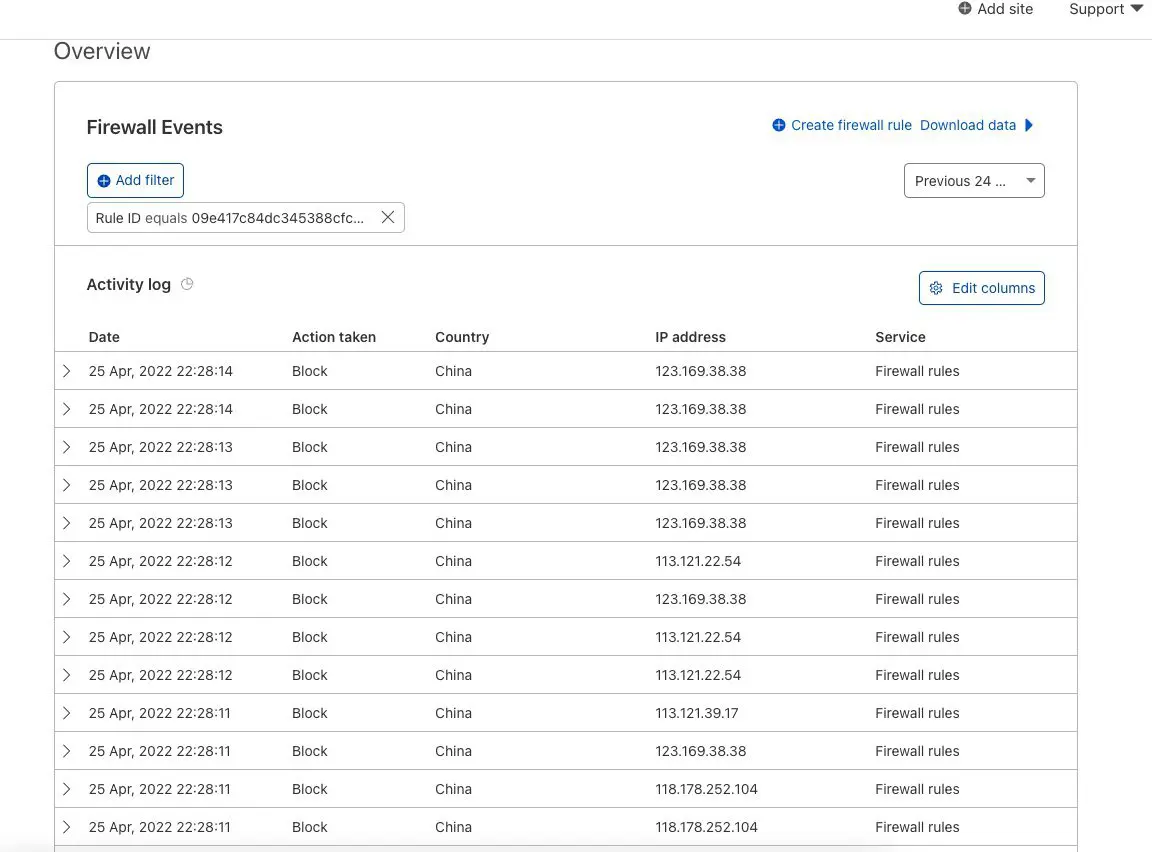
Block all access, and allow only certain countries
This is similar to blocking by specific countries, but the only difference is that if there are many attacking IPs coming from many different countries, you cannot block each country. Instead, you will allow some countries you want, will block the rest.
Specifically, you need access Security >> Firewall Rules >> Create firewall rule.
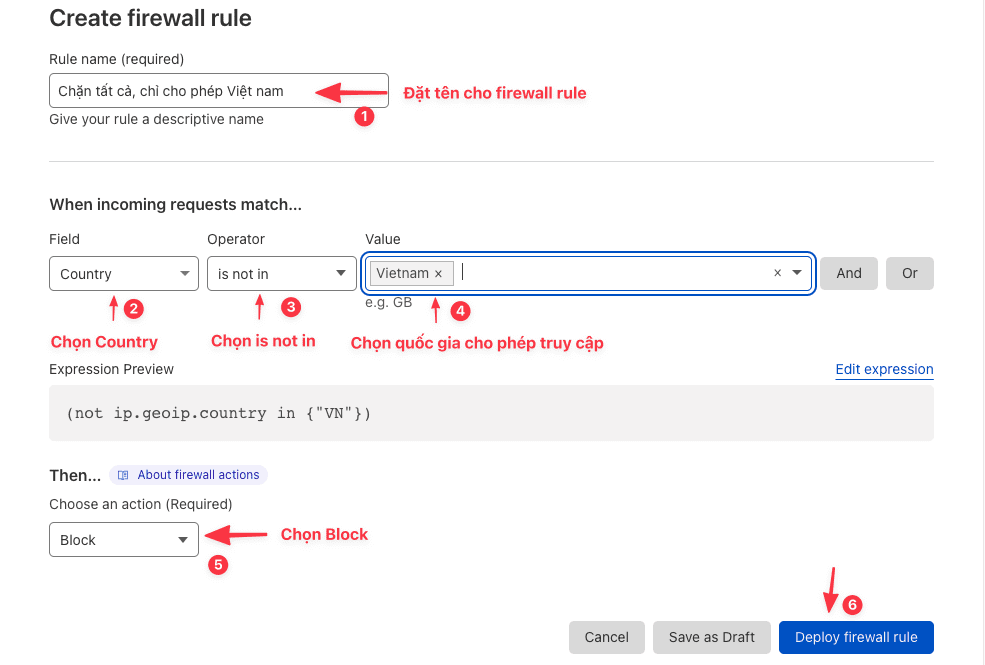
Once set up, the result will be as shown below:
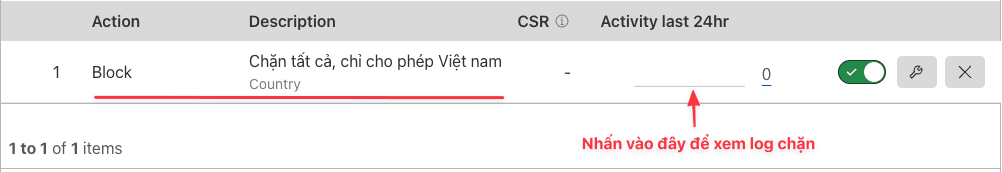
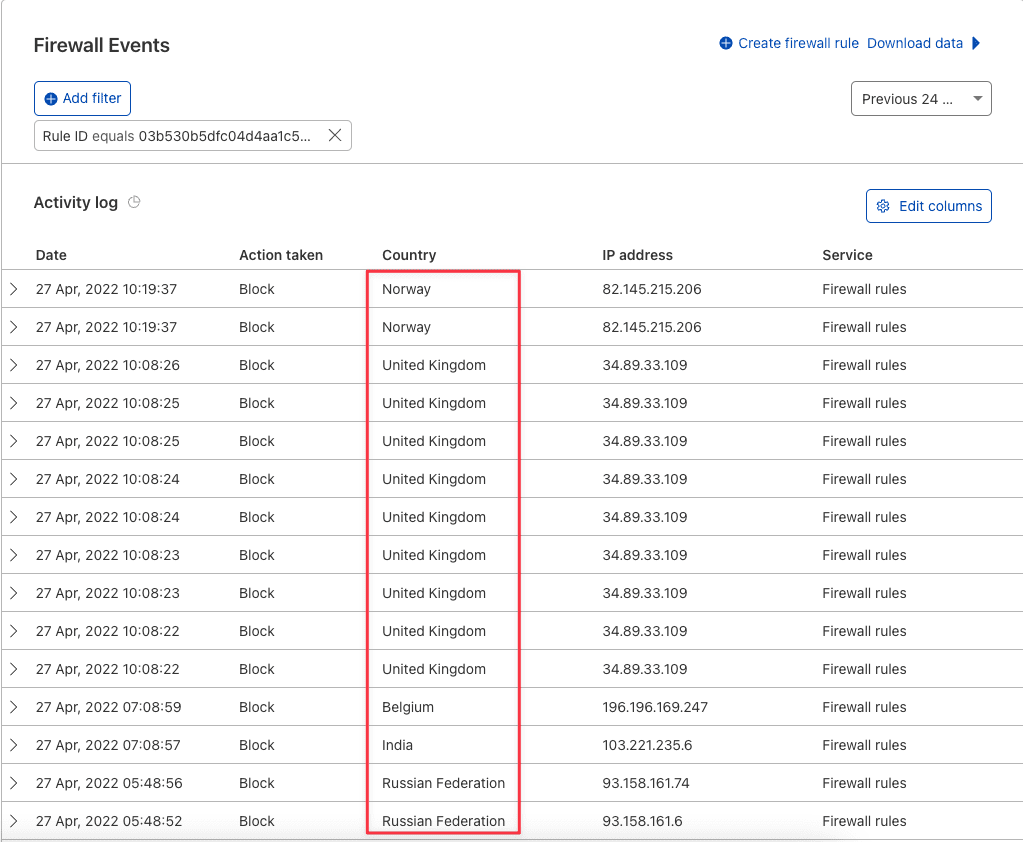
Block by IP
When attacked with a small number of IPs and have identified the exact attacking IP, you should block each IP. However, we should not block the country because it will affect the website’s traffic.
Specifically, you need access Security >> Firewall Rules >> Create firewall rule.
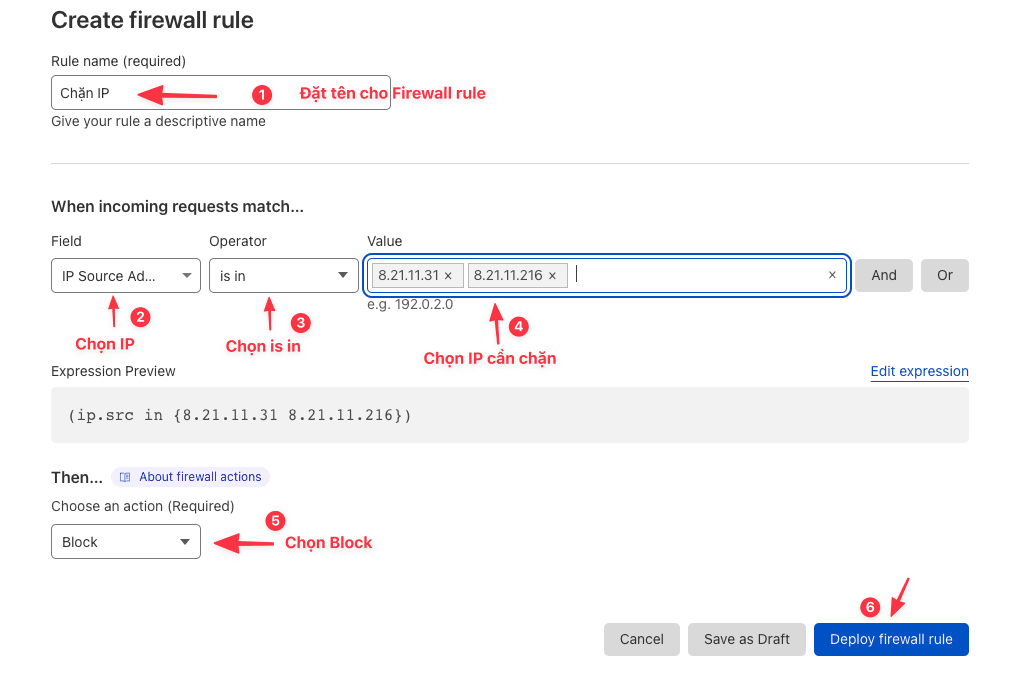
Once set up, the result will be as shown below:
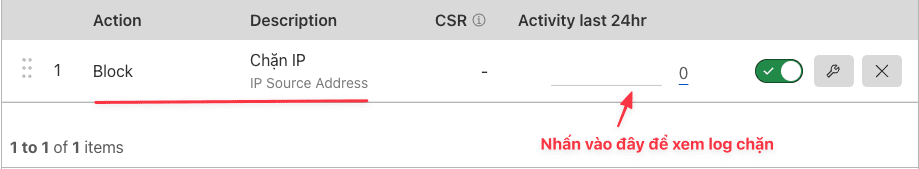
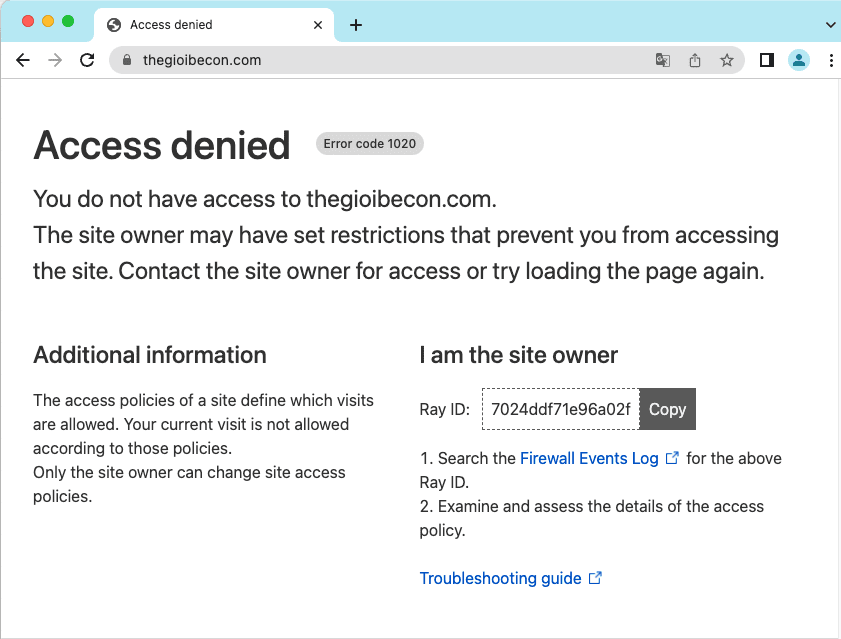
When you finish blocking, the blocked IP from accessing the website will give an error:
Enable Captcha confirmation
With this method, you will need to use it when attacked by the domestic IP. For example, you are in Vietnam, customers and users accessing the website are Vietnamese, you should not block access because it will directly affect your business.
Therefore, in this case, you need to enable Capcha validation for your website, that is, when the user visits the website, then Cloudflare will display the Capcha authentication form for the user to confirm before accessing the website, which helps Cloudflare determine if this user is real or a robot.
Specifically, you need access Security >> Firewall Rules >> Create firewall rule.
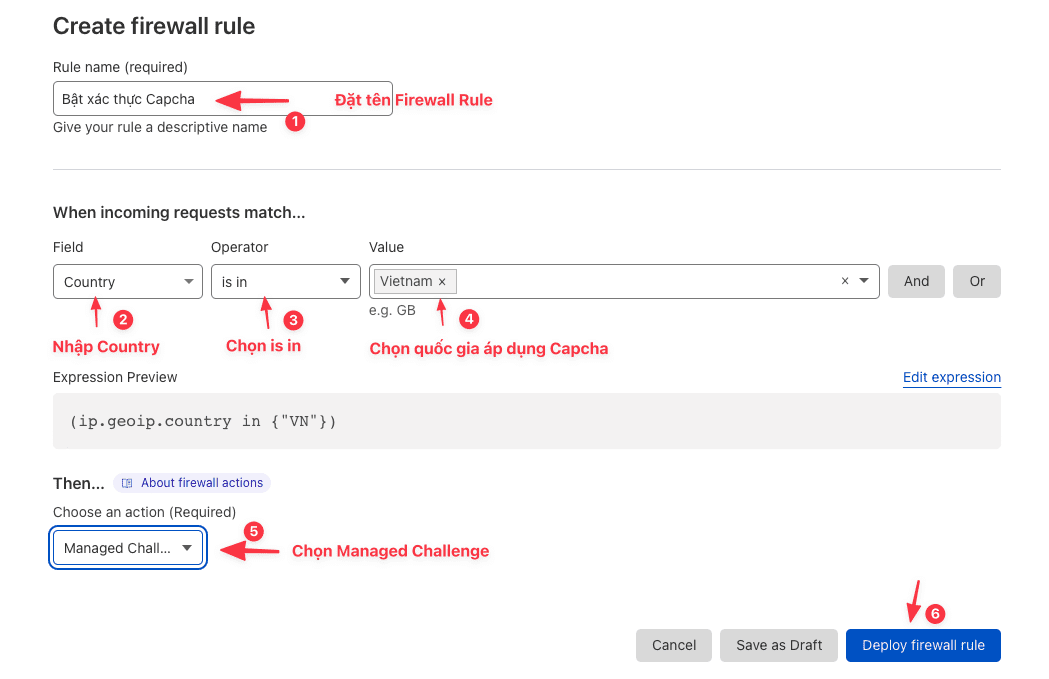
Once set up, the result will be as shown below:
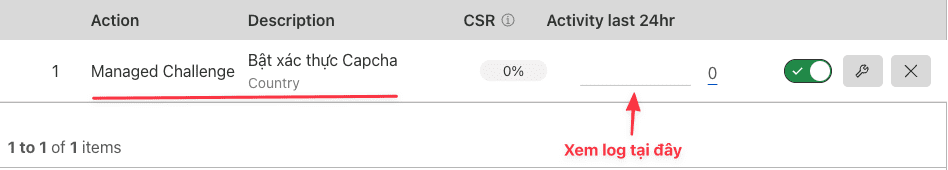
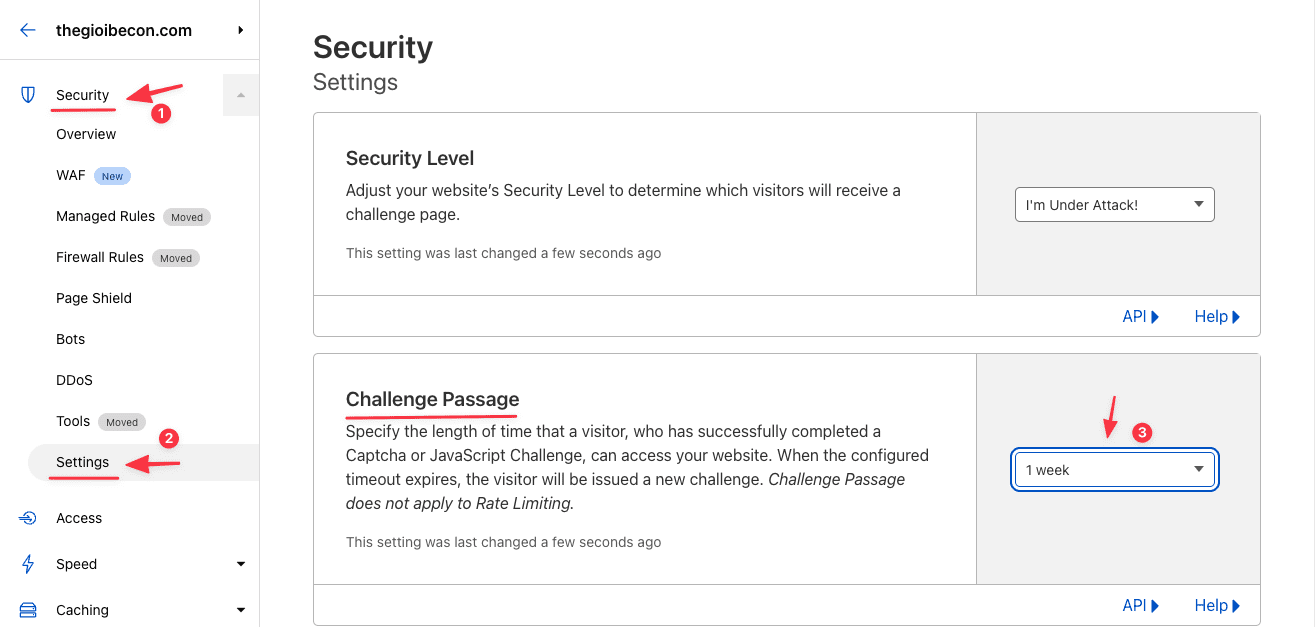
In this Capcha setting, a feature that allows the previously authenticated IP client to pass the Rebot authentication step on subsequent visits. And you can set the time to bypass the authentication according to your needs, here I will choose the time to be 1 week, and after 1 week that IP client will need to re-authenticate the Captcha.
To configure, you access Security >> Setting >> Challenge Passage and choose the time you need.
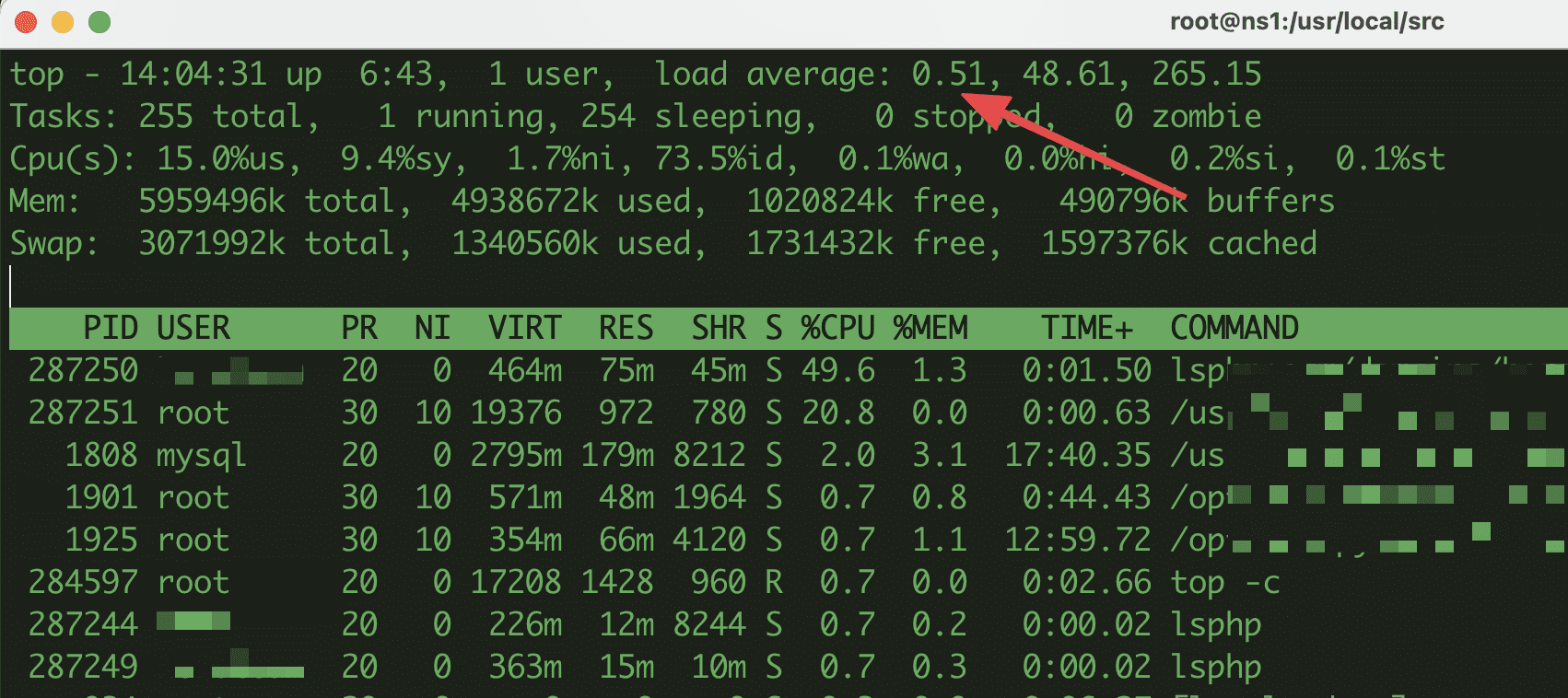
After applying some of the above methods, now I have solved the problem on my VPS. The server’s load average is stable again.
Turn on anti-Bot mode
CloudFlare adds an important feature that helps a lot with websites that often suffer from DDoS, which is setting a bot prevention level. This feature will give you the right to allow access or block all strange bots from accessing the website, excluding Google bots .
Bots will be classified by CloudFlare into 3 levels including:
- Definitely automated : Bots that have been confirmed to be completely automated, are mostly spam bots or bots that crawl data from less popular tools, this type should be completely blocked.
- Likely automated : Is a list of bots that CloudFlare believes are still automated but may be less common in danger.
- Verified bots : Bots that CloudFlare confirms are verified, causing little or no impact on the website. This list will include bots from Google, Microsoft, Amazonbot, GPTBot,…see the full list here .
To customize the bot blocking level, access the Security = section> Bots and setup as shown below.
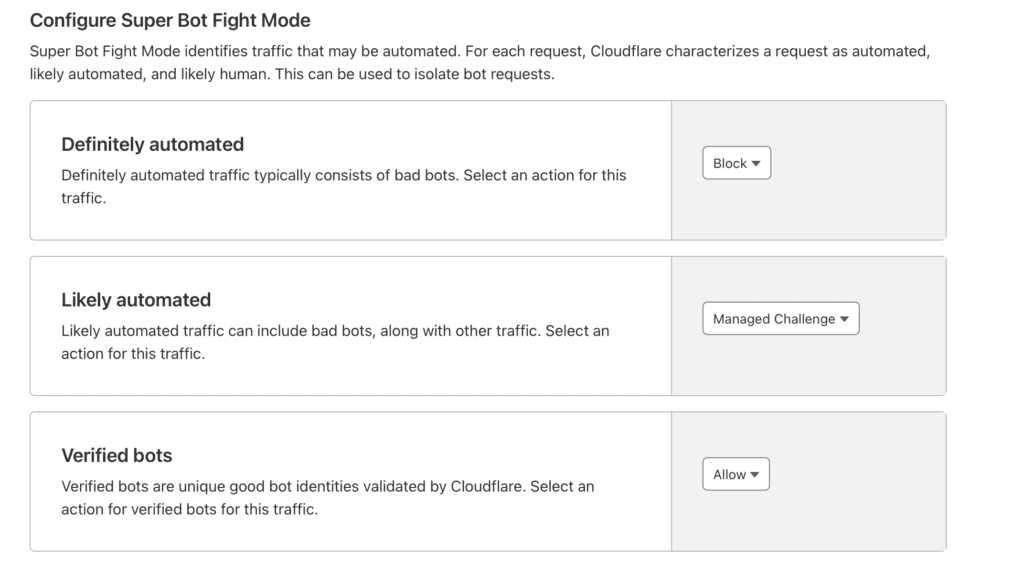
In case you get attacked too much, try putting Likely automated on the Block action to limit it.
Thus, AZDIGI has shown you how to identify DDoS attack types and effectively use Cloudflare’s Firewall to prevent DDoS attacks. Through this article, you probably understand the benefits that Cloudflare brings, even though it is only a free version, it supports users extremely well. However, if you are a large enterprise and need more features from Cloudflare, you can refer to using Cloudflare’s paid version.
You can refer to other instructions at the link below:
If you need assistance, you can contact support in the ways below:
- Hotline 247: 028 888 24768 (Ext 0)
- Ticket/Email: You use the email to register for the service and send it directly to: support@azdigi.com.

